Blog
30-11-2021
Computer Security Day
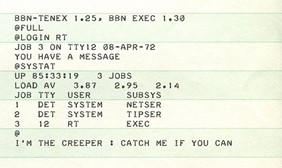
In 1971, the highly skilled scientists developing the ARPANET network - the predecessor of the Internet - saw the following message appear on their computers:
This was the first computer virus in history, which was called the "Creeper".
1von Neumann, John; Burks, Arthur W. (1966), Theory of Self-Reproducing Automata.
"I'm the Creeper: catch me if you can"
This was the first computer virus in history, which was called the "Creeper".

The "Creeper" was nothing more than a proof of concept by the skilled programmer Bob Thomas, who had only the intention to demonstrate John von Neumann's1 theory - from the late 40's - that it was possible to create software that traveled from computer to computer in a computer network autonomously. Bob Thomas successfully achieved his goal and boosted the creation of tools to protect computers and networks, such as antivirus.
Since then, computers and the internet have evolved, and have become indispensable for the development of activities in the most diverse sectors and for connecting people from the most different cultures and communities.
With the democratization of computers and the internet, more computer viruses with a greater impact on the daily lives of organizations and citizens have emerged, culminating in the "Morris" virus, which in 1988 made almost 10% of the ARPANET network unavailable.
This event created, in the United States, a great need to make companies and citizens aware of the dangers and threats of new technologies and the importance of adopting more cyber-secure practices.
Thus was born the day, which we celebrate today, dedicated to computer security.
How can we celebrate this day?
Use strong passwords: We should use long passwords (at least 9 characters) and include uppercase and lowercase letters, symbols and numbers. We should not put personal information in our passwords, such as our date of birth or soccer club.
Two factor authentication: Having one strong password may not be enough these days, so multi-factor authentication is recommended. Multi-factor authentication adds an extra layer of security to the usual password. So whenever possible, we should set up our accounts to use a second factor such as SMS or digital token.
Keep your computer up to date: It is important to keep the software on our devices up to date. We should regularly update our devices. Updates have security patches that help us to be better protected against known bugs and/or vulnerabilities.
Encrypt and back up data: Cybercriminals are not always looking to steal our data. Sometimes, the goal is simply to encrypt or delete it. Therefore, you should always encrypt your data and, back it up regularly. Attention, you should store your backups on another device or even in an online cloud.
Regular security checks: You should perform vulnerability audits of your systems and applications on a regular basis. This will help preventively identify any security weaknesses that could jeopardize the availability, integrity or confidentiality of your information.
Make all employees aware: It is essential to make employees aware of the dangers and threats of cyberspace. People remain the weakest link in the chain of a cyber attack.
1von Neumann, John; Burks, Arthur W. (1966), Theory of Self-Reproducing Automata.
Please note: the articles on this blog may not convey the opinion of .PT, but of its author.
Back to Posts